Announcement: We are delighted to announce that the names of the finalists have now been communicated to the Placement Officers. We would like to extend our heartfelt gratitude to everyone who took part in this process. Thank you once again for your participation and commitment!
Barclays India is excited to announce the return of ‘Hack-O-Hire’ where Innovation, Creativity, and Collaboration will shine. Whether you're a seasoned coder or just getting started, this is your chance to make an impact and solve real-world problems.
No matter your skill level, ‘Hack-O-Hire’ is about pushing boundaries, learning, and having fun together. It’s a place to dream big, think out-of-the-box, and create solutions that can change the future.
This hackathon is more than just an event. It’s a celebration of your creativity, your curiosity, and your drive to make something meaningful. You’ll face challenges, and you may stumble along the way, but remember—that’s where real growth happens.
So, grab your laptops, rally your teammates, and let's make something amazing happen!
Key Pointers
- Teams should consist of 3 to 5 members (with at least one female member). Only the team leader should register on the HackerEarth platform.
- Only 2nd and 3rd year students are eligible.
- Streams: CS, IT, E&TC, AI/ML, Data Science.
- Each participant can be part of only one team. Multiple registrations/team entries will be disqualified.
- Each team can submit only one solution, meaning they must choose only one problem statement.
- Barclays will not be providing any environment or tools for the hackathon, and students will be expected to use their own laptops..
- The overall size of the documents (Doc,PPT,PDF etc.) for the initial submission should not exceed 45 MB.
- No code to be uploaded as part of initial submission.
In-Person Finale
- For Pune and Mumbai Colleges, the finale will be hosted at Barclays Pune Campus.
- For Chennai Colleges, the finale will be hosted at Barclays Chennai Campus.
- Date: 26th April and 27th April 2025
- Location: Barclays Pune and Chennai Campuses
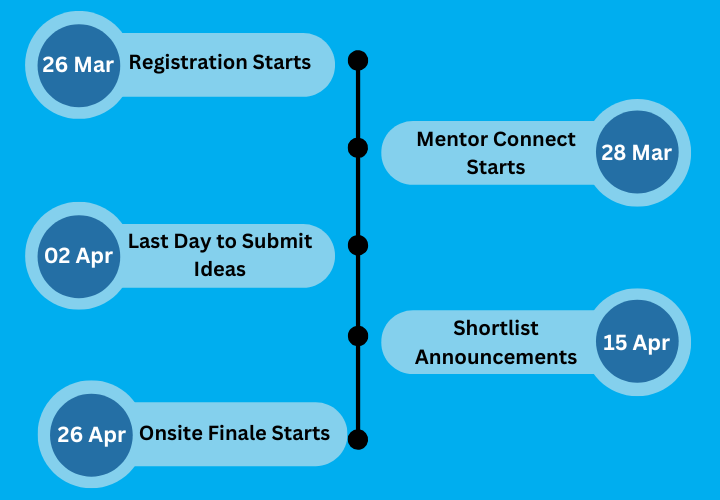
Timelines